Capacity 8 GB – 256 GB
Size With sleeve - H: 78 mm W: 20 mm L: 10 mm
Without sleeve - H: 77 mm W: 20 mm L: 10 mm
Weight With sleeve: 18 grams
Without sleeve: 12 grams
Data Transfer Speed Reads up to 130 MB per second; writes up to 118 MB per second
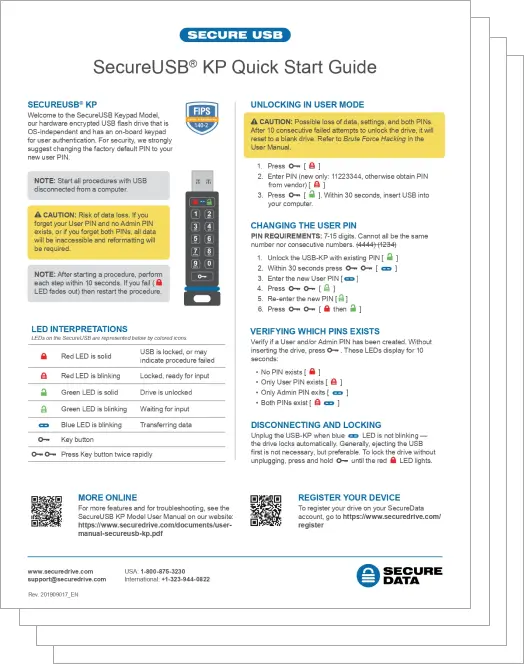
Keypad Wear-resistant keypad
Security Module Validation FIPS 140-2 Level-3 Validated
Authentication method User authentication via onboard keypad
Interface USB 3.0/3.1 gen1/3.2 gen1
Data Protection Real-time military grade XTS-AES 256-bit full-disk hardware encryption
Waterproof IP68 Certified (in Sleeve)
Tamper-evident Protected with epoxy compound to prevent physical access to the device through tampering
Brute-force defense Erases all data after 10 consecutive, incorrect PIN entry attempts
Immune to Bad USB Yes; firmware updates not allowed
Roles/Permissions 1 Admin / 1 user
Read Only Mode Yes
Inactivity Auto-lock Predefined times between 1 and 60 minutes
OS Compatibility Microsoft Windows, macOS, Android, Linux, Chrome, Thin Clients, VMWare, Citrix Embedded Systems (no software or drivers needed)
Regulatory Approvals FCC, CE
Warranty 3-year limited
When referring to drive capacity, one gigabyte (GB) equals one billion bytes. One terabyte (TB) equals one trillion bytes. Your computer’s operating system may use a different standard for measurement and report a lower capacity.