CMMC 2.0 is a cybersecurity program that streamlines the previous model (CMMC 1.0) and offers better functionality and collaboration. It was developed by the U.S. Department of Defense (DoD) to protect sensitive information that they share with defense contractors and subcontractors in the defense industrial base (DIB). It hasn’t gone into effect yet, but, once it does, all contractors will have to adhere to CMMC 2.0 guidelines in order to be eligible for contracts.
The final CMMC 2.0 rule will likely be published in the first half of 2025. While this is subject to change, it’s important to start preparing now. It can take anywhere from a year to 18 months to become assessment-ready.
In this post, we explain what CMMC 2.0 is and who it applies to, as well as what you need to do in order to comply.
What is CMMC 2.0?
CMMC stands for Cybersecurity Maturity Model Certification. It is a set of cybersecurity requirements for defense and industrial base contractors and partners. These requirements are designed to protect sensitive unclassified information that is shared with defense contractors. The Department of Defense (DoD) developed this CMMC framework to protect information that affects national security. This is because the Defense Innovation Board (DIB) sector is a frequent target of cyberattacks.
CMMC 2.0 is the new iteration of CMMC, after the first change in CMMC 1.0. In November 2021, the DoD announced that CMMC 2.0 will be implemented through a rulemaking process, after which it will become a contract requirement.
Until CMMC 2.0 becomes a formal requirement, contractors and subcontractors still need to comply with Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204.7012. This clause is a set of government regulations that outline minimum cybersecurity standards. This clause is its own distinct set of rules, though it overlaps with some clauses from CMMC, FAR 52.204-21, and NIST 800-171 (which is a building block for CMMC).
The CMMC 2.0 rule was published in the Federal Register on December 12, 2023, with a comment period running through February 26, 2024. The final rule is set to be published in the first half of 2025, and will likely have a multi-year phased rollout. But CMMC compliance takes time to achieve, so it’s important to start working toward it as soon as possible.
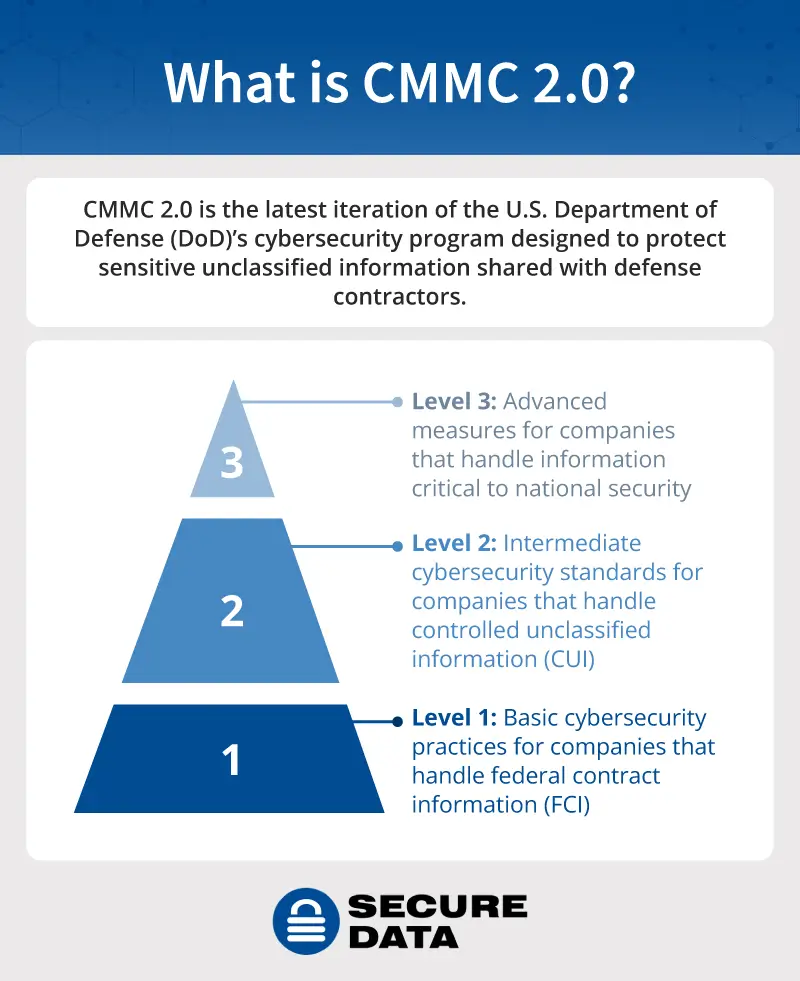
The new CMMC 2.0 model has 3 compliance levels compared to the previous version with 5 levels. In the old 1.0 version, levels 2 and 4 are intended as transition stages. The 2.0 version simplifies the levels and now only has 3.
CMMC 2.0 Levels:
CMMC 1.0 vs CMMC 2.0
CMMC 2.0 improves on CMMC 1.0 in many ways:
- Streamlined model: 2.0 simplifies the previous model from five to three compliance levels.
- Direct map to National Institute of Standards and Technology (NIST) cybersecurity standards: CMMC 1.0 levels three to five were based on NIST SP 800-171. CMMC 2.0 simplifies this by making level two align with NIST SP 800-171 and level three align with NIST SP 800-172.
- Lower assessment and compliance costs: CMMC 2.0 allows companies at level one and level two to comply through self-assessment, lowering the cost of entry for smaller businesses.
- Better collaboration: Companies may also become certified through Plans of Action & Milestones (POA&Ms), which provide roadmaps to identify and address system weaknesses.
- More flexibility: If necessary, the government can waive some CMMC requirements under certain limited circumstances.
Who needs to comply with CMMC 2.0?
Any DoD contractor or subcontractor who plans to bid on DoD contracts that include the CMMC clause will have to become CMMC-certified in order to qualify. Each individual contract will explain which level of compliance a contractor needs to meet. This can vary from job to job.
CMMC 2.0 is designed to account for how information moves through a multi-tier system or supply chain, keeping controlled unclassified information (CUI) and federal contract information (FCI) protected at any stage of a DIB project.
For this to be effective, CMMC must apply to all parties in the supply chain, including:
CMMC 2.0 Model Structure and Requirements
CMMC 2.0 streamlines requirements, with only three cybersecurity levels. Each level is aligned with common cybersecurity standards.
The levels and their requirements become more advanced depending on the type and sensitivity of information a company typically handles. The levels are also cumulative — for a company to achieve one level, it must not only meet that level’s requirements but also the requirements of the previous levels.
The three levels of CMMC 2.0 are:
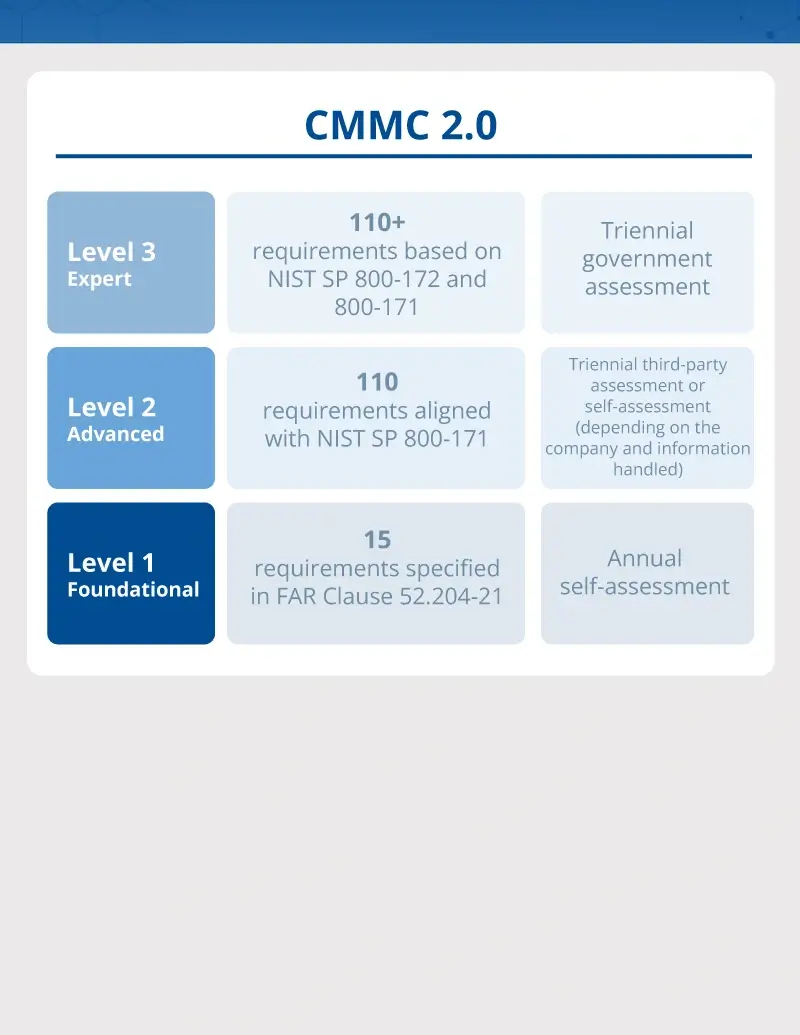
CMMC Level 1: Foundational
Level 1 is the most basic, designed for companies that handle FCI — information that is not highly sensitive, but still requires protection and is not intended for public release.
This level contains 17 individual practices, corresponding to the safeguarding requirements outlined in Federal Acquisition Regulation (FAR) clause 52.204-21. Level 1 companies are allowed to conduct annual self-assessments to demonstrate compliance.
Here’s what the requirements cover:
- Restricting system access: Only authorized users can access information systems, processes, and devices. Companies also need to limit what transactions and functions these users can perform.
- Managing external connections: Companies must monitor and control connections to external information systems and what content is shared on public systems.
- Identifying users and devices: Companies must identify and verify all users and devices that interact with the system before they are granted access.
- Controlling physical security: Companies need to limit physical access to the system, and securely dispose of or sanitize any media devices that might contain sensitive information, like encrypted hard drives.
- Monitoring all communications: Companies need to constantly monitor all internal and external communications, which involves using subnetworks for public parts of the system, regularly checking for and fixing system flaws, keeping security software updated, and frequently scanning the system and files for threats and malware.
CMMC Level 2: Advanced
Level 2, the intermediate level of cybersecurity standards, is designed for companies that handle CUI — information that is sensitive and requires protection, but that isn’t classified. This level contains 110 individual practices that align with NIST SP 800-171, guidelines from the National Institute of Standards and Technology on protecting CUI.
Some companies at this level are allowed to conduct self-assessments. Companies handling more sensitive information, however, have to submit to third-party compliance assessments.
Companies at Level 2 will have to meet both the requirements of Level 2 and Level 1. Here’s what the Level 2 requirements cover:
- Monitoring and auditing: Companies must maintain detailed logs of system activity, monitor and manage physical access, and supervise visitors within secure areas.
- Managing configurations: Companies have to manage and securely configure their information systems to ensure they have the proper setup for protecting CUI.
- Responding to incidents: Companies need to develop plans and implement responses to cybersecurity incidents, including identifying, reporting, and repairing system flaws promptly.
- Maintaining systems: Companies must regularly perform maintenance on their information systems to ensure that they’re sound and secure.
CMMC Level 3: Expert
Level 3, the most advanced level, is designed for companies that handle controlled unclassified information, often critical to national security. This level contains over 110 individual practices that align with NIST SP 800-172, the supplementary guidelines to NIST SP 800-171 that involve enhanced security requirements.
Due to the sensitive nature of the information they handle, companies at this level have to undergo government assessments to ensure compliance.
Here’s what Level 3 requirements cover (in addition to requirements from Levels 1 and 2):
- Combating advanced persistent threats (APTs): Companies have to implement guidelines to protect CUI from sophisticated cyber threats and attacks.
- Enhancing basic security: Companies must build upon the basic security requirements they derive from NIST SP 800-171 with additional protective measures.
- Ensuring confidentiality, integrity, and availability: Companies should take measures to not only keep CUI confidential but also ensure its integrity and make it available to necessary parties.
- Maintaining flexibility: Companies have to adapt to changing or unique security requirements and apply measures based on federal agency missions, business needs, and risk assessments.
- Protecting critical assets: Companies must apply security requirements to nonfederal systems that handle CUI associated with federal programs or high-value assets.
- Developing resilient architectures: Companies need to create systems and operations that can resist and survive cyber-attacks.
- Strategizing for comprehensive protection: Companies must develop comprehensive strategies to safeguard CUI against unauthorized disclosure, modification, and disruption.
Types of assessments
Compliance with CMMC 2.0 entails regular assessments to ensure that effective security control measures are in place to protect sensitive information through all stages of a project.
Level 1 self-assessments and Level 2 third-party assessments include:
- Interviews: Company representatives or third-party auditors interview staff at various levels to determine how well they implement security practices, as well as if they have adequate training, resources, and planning.
- Examination: Auditors examine documents, mechanisms, and activities, such as policy, planning, procedure documentation, and training materials, as well as system, network, and data flow diagrams.
- Testing: Where applicable, auditors use demonstrations to provide evidence that practices are being met.
The assessments have three possible results for each practice, each provided with supporting evidence:
- Met
- Not met
- Not applicable (N/A)
Self-assessments
Level 1 contractors and level 2 contractors who don’t handle information critical to national security are required to perform annual self-assessments. Each self-assessment has to come with an affirmation from a senior company official that states the company is successfully meeting its security requirements. Self-assessments and affirmations also may need to be registered in the Supplier Performance Risk System (SPRS).
There is a Level 1 Self Assessment Guide available (opens as a PDF) with full criteria.
Third-party assessments
All Level 2 contractors who manage information that is critical to national security need to undergo a CMMC third-party assessment. Independent CMMC assessor organizations (C3PAOs) conduct these third-party audits. C3PAOs are accredited by the Cyber AB, formerly known as the CMMC Accreditation Body, and are required to comply with ISO/IEC 17020.
The third-party assessment process doesn’t happen automatically. Contractors are responsible for making sure it gets done. The C3PAO just administers the assessment and uploads it when it’s complete.
During a Level 2 assessment, a certified assessor verifies that the contractor has properly implemented security practices using a variety of techniques, depending on the information involved. Although there are similarities, the process for Level 2 is more detailed than for Level 1, requiring more comprehensive documentation, evidence of implementation, and demonstration of the company’s cybersecurity processes.
There is a Level 2 Assessment Guide available (opens as a PDF) with full criteria.
Government assessments
Level 3 companies that handle information critical to national security will need a government-led assessment. The requirements for these assessments are currently still in development, as is the official CMMC Level 3 Assessment Guide.
3 Tips to Build a CMMC 2.0 Compliance Strategy
Preparing in advance for CMMC 2.0 can help you deal with the complexities of implementation, giving you the best chance of securing contracts once it’s rolled out. Here are some tips to start building your compliance strategy.
1. Understand which CMMC 2.0 level you need to comply with
The first step toward compliance is identifying which level you have to comply with. Familiarize yourself with the three levels and the requirements of each. That will help you determine what type of information you handle, whether that includes CUI or just FCI.
All contractors who handle FCI need to meet Level 1 requirements. If you handle CUI as well, you’ll need to comply with Level 2. Only those who handle CUI critical to national security will need to comply with Level 3.
2. Conduct a gap analysis
Next, evaluate your current cybersecurity practices against what CMMC 2.0 requires for your level. The analysis should cover all relevant areas, including policies, procedures, access control, and employee training, to help you see where you’re on target and where you might be falling short.
Based on the results of your analysis, prioritize the areas of improvement that are necessary to meet CMMC 2.0 requirements. This could involve updating policies, training employees, or acquiring new hardware. Allocate the resources you need to take action, and systematically implement measures to get your company up to speed.
3. Track the flow of FCI and CUI
Keep in mind that only the part of your company that handles FCI and/or CUI is within the scope of these requirements and required to comply. This means you can create a separate environment (physical or digital, or both), also called a security enclave, to house these activities and make compliance efforts less time-consuming and expensive.
This process requires building an inventory of your assets, tracking which exist on your network, and categorizing them based on whether they handle FCI or CUI. You can use this to create a network diagram and visualize the environment.
Keeping CUI and FCI protected requires robust data encryption methods. Make sure that any data stored on USB or external hard drives and cloud storage, or transmitted over any networks, is encrypted using industry-standard encryption protocols.
Secure your data
Using reliable and secure hardware is not only an important step toward CMMC 2.0 compliance — it’s also a necessary safeguard against cybersecurity attacks. From encrypted flash drives and external drives to digital forensics and data recovery services, Secure Data has what you need to keep your sensitive data safe.
Contact us today for an expert’s insight on how we can help keep your data safe.